OS command injection vulnerability in Huawei optical network terminal
- 929
- 98
OS command injection vulnerability in Huawei optical network terminal
- By huaweicomputers
- 02/05/2022
JPCERT Coordination Center (JPCERT / CC: Japan Computer Emergency Response Team Coordination Center) announced on August 17th, "JVN # 41466618: Huawei EchoLife HG8045Q OS Command Injection Vulnerability", Huawei's optical network terminal "EchoLife HG8045Q" I told you that there is a vulnerability in. Exploitation of this vulnerability could lead to the execution of some OS commands on a device affected by an attacker.
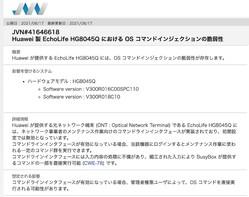
According to JPCERT / CC, the EchoLife HG8045Q has a command line interface for maintenance work by network operators. Network operators can use this interface to execute various commands for maintenance work. There is a flaw in the processing of the input contents of this command line interface, and it is possible to execute some of the commands provided by the BusyBox tool by maliciously crafted input. BusyBox is a general-purpose command tool for embedded Linux.
This vulnerability is only affected if the maintenance command line interface is enabled. It is disabled by default on the EchoLife HG8045Q.
As a countermeasure, updating to the following version provided by the developer is mentioned.
The basic score of CVSS v3, which indicates the severity of the vulnerability, is "6.8", and it is classified as the third "warning" from the top in the five stages.