ASCII.jp No need for a firewall full of holes anymore
- 1255
- 98
ASCII.jp No need for a firewall full of holes anymore
- By huaweicomputers
- 21/04/2022
Internet attacks have become more sophisticated and complex, and existing firewalls can no longer handle them. Why did the power of the firewall, which was an iron wall, weaken? We will carefully verify it.
Security threats spreading with the rise of web applications
The rise of web applications has been remarkable in recent years. The conversion of business applications to the Web has been promoted since the latter half of the 1990s, but since the advocacy of "Web 2.0" in 2004, the trend has been accelerating at a stretch. With the recent evolution of Ajax and rich client technologies, operability similar to that of local applications has been realized even on a Web browser. "Web applications aren't easy to use" is already becoming a thing of the past.
Under these circumstances, SaaS that uses Web applications such as Google Apps and Salesforce CRM that adopt the latest technology for a monthly fee has become common, and recently there is a growing movement to utilize services for individuals such as Twitter and Facebook in business. Is becoming. In addition, applications that require installation on a PC are increasingly interacting with other nodes via a network or linking with the cloud, and applications that are used purely on a PC or within a LAN are no longer available. It can be said that there is.
However, the rise of these network applications poses a major threat to corporate information management. This is because there is an increasing possibility of causing intrusion of malicious programs called viruses and spyware from the outside, spam emails that cause inconvenience, and conversely, leakage of business information and personal information (Fig. 1).
Figure 1 Many applications utilize the 80/443 port
Security incidents such as virus infection by P2P software, leakage of business information to the outside by SNS, Web falsification by drive-by download attack, site attack by bot infection, etc. occur every day. In addition, there are many cases in which the reputation of companies and products is damaged due to incorrect use of SNS. There are numerous examples of publicly disclosing the company to which they belong, blaming competing products by name, and publicly tweeting dissatisfaction with customers. Even with the well-known cloud tools "DropBox" and "Skydrive," not all employees upload all of their company's confidential information.
On the other hand, many administrators think that "the company has a firewall installed, so you can rest assured!" However, firewalls developed for the Internet in the 1990s are no longer playing a role. Let's see why.
Old firewall where you can't see the application
The role of the firewall is access control and logging. In other words, for the input packet, it is judged whether it can pass or not, and the access log is recorded. This prevents attacks from the Internet from reaching the LAN and public servers, and controls that malicious packets are not sent from within the LAN.
Traditional firewalls use filtering rules that are conditioned by combining the IP address, port number, protocol number, etc. of the destination and source to determine whether or not a packet can pass.
For example, the communication of the Web browser sends the request of the PC in the LAN to the Web server on the Internet to the HTTP port 80, and the Web server also returns the response to the PC in the LAN via the same port. It becomes the flow. Therefore, if only communication on the Web is permitted, the rule that HTTP port 80 from LAN to the Internet is OK and the others are blocked is applied. As a result, only HTTP Web browsing can be permitted from the LAN to the Internet.
However, most web applications in the world use HTTP or HTTPS, that is, ports 80 and 443. In fact, Salesforce CRM, Twitter, Facebook, YouTube, and applications like Google Apps such as Gmail, Google Calendar, and Google Docs all use port 80/443. Since multiple applications use the same port, the port number cannot be used to identify which application.
In addition, there are many applications that cross the firewall with advanced methods as well as port 80. For example, Skype will automatically search for and use a free port, tunnel the communication itself with SSL, or use another Skype node that can communicate as a proxy. The application itself is built on the assumption that it will cross a firewall. In addition, anonymous proxies such as TOR (The Onion Router) and Ultrasurf, which have become a hot topic these days, and tunneling applications such as Hamachi can easily go beyond firewalls and URL filtering. These tools and sites are easy to find by just searching, so end users can easily get to use them. Just allowing HTTP web browsing will allow most applications to bypass the firewall.
Anonymous proxy that is easy to use just by entering the URL
In addition, it is difficult to collect logs with the old firewall. For example, when checking access to 2channel, you must first identify the URL addressed to 2channel and identify who the sender's IP address is. If it's a log one day ago, you might be able to do this manually, but if it's a year ago, you're out of luck. In addition, anonymous proxies and tunneling applications that disguise the source can be used to completely bypass the firewall. In the first place, the huge amount of logs themselves are worthless, and they are meaningful only when communication trends and attacks are properly detected. Even if many companies install firewalls, the reality is that they have not been able to analyze application usage status and attack trends and utilize them for countermeasures.
Another point I would like to point out is that the relationship between the client and the server is breaking down. As you know, HTTP communication on the Web consists of a request to a server and its response. However, many of them nowadays operate as Web servers on client PCs. In this case, even if you scrutinize the log, it is extremely difficult to follow the flow of data.
No for existing firewalls and UTM approaches!
Koichiro Otobe of Palo Alto Networks recommends a move to a "next-generation firewall" that warns of the limitations of existing firewalls and enables application visualization and control. Mr. Otobe says, "If you can't control access, it's difficult to collect logs. If you can't manage it, it doesn't make sense to install that firewall."
Photo 2 Mr. Koichiro Otobe, General Manager, Technology Division, Palo Alto Networks
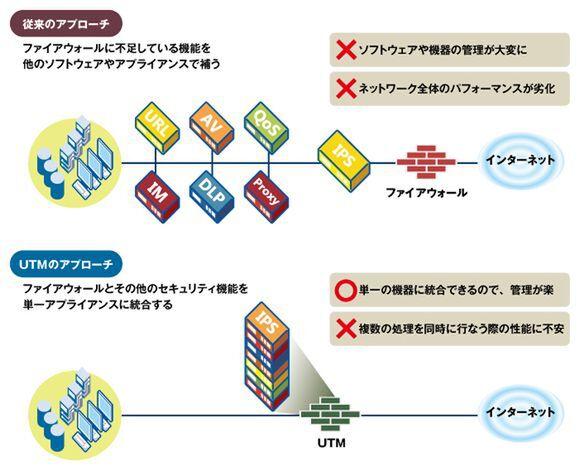
Currently, many companies have installed firewalls at the boundary between LAN and the Internet, and to supplement them, they have installed dedicated devices such as antivirus, IPS, and URL filtering (Fig. 2). The reason why we have to adopt such a wasteful configuration is that the scope of conventional firewalls and security products is narrow. Firewall is IP address and port, antivirus software is virus, URL filtering is URL only. It is difficult to detect complex threats with these individual measures.
Figure 2 Differences between traditional firewall and UTM approaches
But what about UTM (Unified Threat Management), which integrates security features such as firewalls, IPS, antivirus, and web filtering into a single piece of hardware? It is true that UTM has countermeasures against threats, but since there are multiple engines, performance degradation is inevitable. Even though the firewall throughput is super fast, some products even drop the throughput by two orders of magnitude when used as a UTM with multiple features turned on. In addition, it is necessary to set a policy for each function, and there are many products that can only be selected by choosing between blocking and passing control.
On the other hand, Palo Alto Networks' next-generation firewall "PA series" has returned to the original purpose of the firewall, which is access control and log collection, and redesigned the structure itself for application visualization and control.
Photo 1 Palo Alto Networks "PA-5000 Series"
Looks like this!You can also see banned applications
Palo Alto Networks is a US IT vendor founded in 2005. Founder Nia Zouk was one of Check Point Software Technologies' developers of Stateful Inspection, the foundation of today's firewalls, and has since been one-secured and the world's first IPS. After the acquisition of OneSecure by NetScreen, he served as CTO of Juniper Networks after the acquisition of NetScreen, and then established PALART in 2005 to develop the next-generation firewall "PA series". A new type of firewall redesigned by the originator who created the prototype of the firewall and knows its weaknesses. The idea is completely different from the rehashing of existing firewalls and the accumulation of functions.
Currently, Palo Alto Networks has an overwhelming share of 78.9% in the domestic next-generation firewall market (Fuji Chimera Research Institute, monetary basis). The market is still in its infancy, but rapid growth is expected in the future.
Next time, why will these application visualizations and controls be possible? Let's take a closer look at the PA series architecture and high-speed processing mechanism.
What is ASCII Club?
To List
To List
Display format: PC ⁄ smartphone